NEW: Damn Vulnerable Raspberry Pi runs on all Pi’s
The touch friendly “driving range” for IoT penetration testing with your Kali-Pi.

Sticky Fingers DV-Pi – pre-configured with vulnerabilities for penetration and privilege escalation.
All DV-Pi’s can be operated with a touch friendly interface or headless via ssh.
Ideal tool for practicing, competitions and live-hacking events.
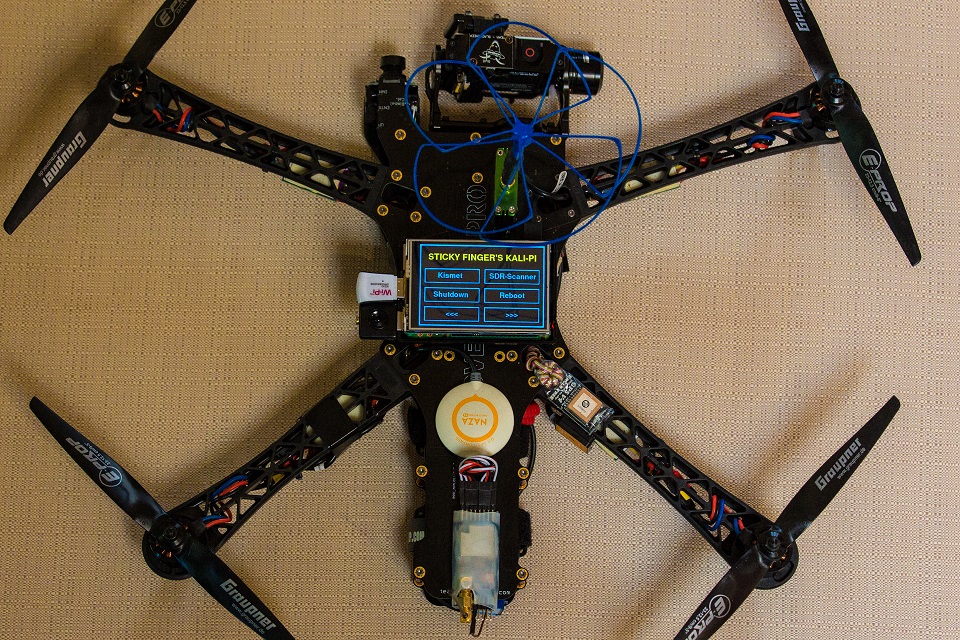
Need a penetration testing platform? Check out Sticky Fingers Kali-Pi
Sticky Fingers Quick Start Guide:
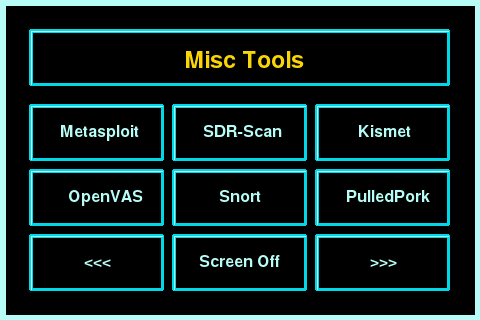
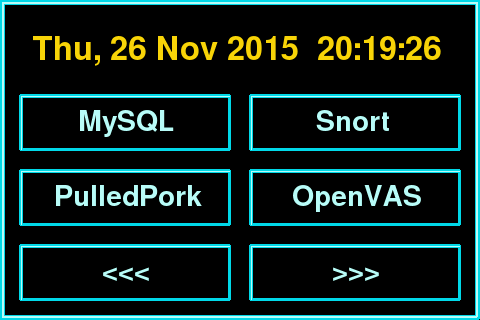
Sticky Fingers DV-Pi images come with the following features out of the box:
- 3GB image ready to go with all common TFT screens
- Re4son Kali-Pi Kernel 4.9 with touch screen support
- Supports Raspberry Pi 0/0W/1/2/3/3B+
- “re4son-pi-tft-setup” tool to set up all common touch screens, enable auto-logon, etc.
- “dv-pi” command line tool for headless operation
- Each image comes with one vulnerability to get in and one vulnerability to get root
- Each image has two proof.txt with a hash to proof successful compromise:
- /proof.txt
- /root/proof.txt
- Just run “re4son-pi-tft-setup” tool for your particular screen and you are up and running.
- Don’t forget to change the password for user “pi” (default: “raspberry”)
“Damn Vulnerable Pi” images:
| Name | Difficulty | Host name | Size | Size and link |
| Sticky Finger’s DV-Pi 2 | medium | dv-pi2.local | 2.5GB | sticky-fingers-dv-pi2 |
| Sticky Finger’s DV-Pi 3 |
easy (ish) |
dv-pi3.local | 2.5GB | sticky-fingers-dv-pi3 |
| More to come | ||||
Anyone interested in creating DV-Pi images can send an e-mail to re4son <at> whitedome.com.au and I’ll share my template image to add some interesting vulnerabilities.
Installation
- Download a dv-pi image and image your microSD card (min 8GB)
- Extend the file system if your card is > 8GB
- Assemble your touch screen (only if you have one, it’s not required)
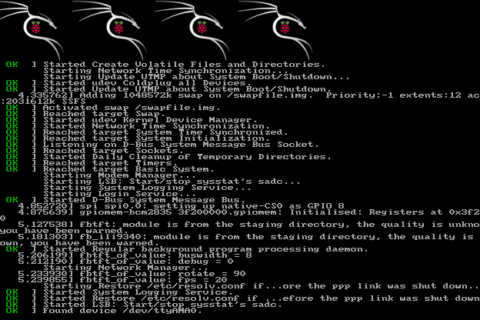
- Boot up your Pi and ssh into it with user “pi” and password “raspberry”
- Change password
- Set up the screen with the re4son-pi-tft-setup tool:
<span style="font-size: 8pt;">cd /usr/local/src/re4son_kali-pi-tft_kernel_4* sudo mount /dev/mmcblk0p1 /boot sudo ./re4son-pi-tft-setup -d #(updates re4son-pi-tft-setup to the latest version) sudo ./re4son-pi-tft-setup -h #(lists all options - pick your screen from the list) sudo ./re4son-pi-tft-setup -t <your screen> -u /root sudo reboot</span>
- Sticky Fingers interface is designed for 3.5″ screens. You can adjust it for 2.8″ via:
cd /home/pi/DV-Pi-Menu git checkout 2.8 #for 2.8" screen
Reboot
Operation
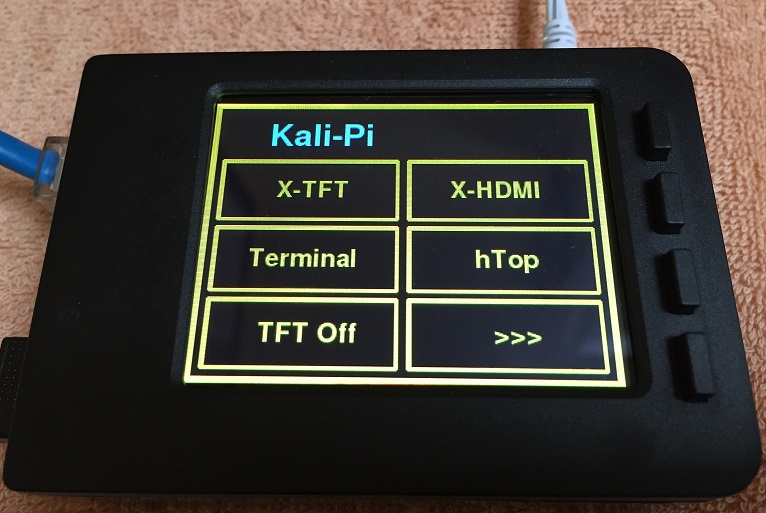
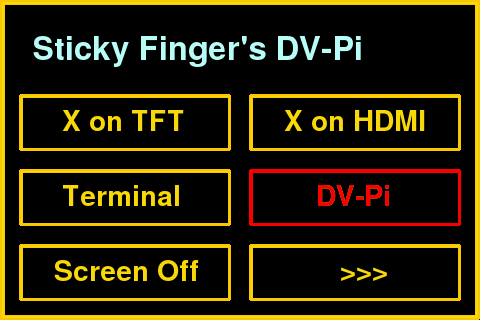
Sticky Fingers Touch interface
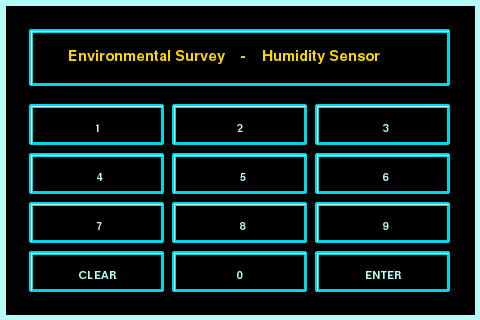
Press “DV-Pi” to start the vulnerable applications (might take a few seconds):
Headless using dv-pi command line tool
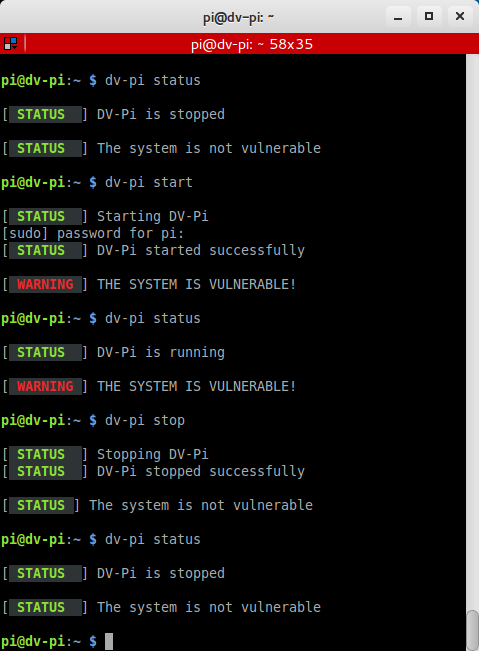
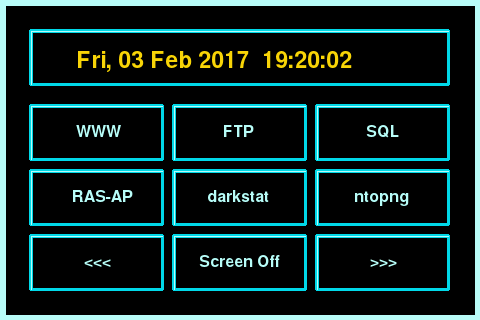
Sticky Fingers DV-Pi can be operated in headless mode using the “dv-pi” tool:
dv-pi status # Show status of vulnerable applications dv-pi start # Start vulnerable applications dv-pi stop # Stop vulnerable applications
Usage
Add dv-pi2 to /etc/hosts on the attacker’s machine
Find the IP address of the dv-pi and add the hostname of the image with the ip address in you /etc/hosts”, e.g.
192.168.137.21 dv-pi2.local
Burn the password for user “pi” and start hacking …
Easter egg
Customer Database
Sticky Fingers DV-Pi contains a database for demonstration purposes, containing 10,000 fake e-mail addresses and credit card details to add an exciting climax to live hacking sessions.
For questions or comments please join the discussion in our forum:
https://whitedome.com.au/forums
Sticky Finger’s Kali-Pi
Check out Sticky Finger’s Kali-Pi if you are in need of a 1337 penetration testing platform.